Ad Lightning’s Q4 2020 Overview of Malicious & Unwanted Ads
Q4 2020 had a different feel to it. Yes, there was the typical holiday push and everything that usually entails. But the digital ad industry was also still finding its bearings from an extremely challenging year, tugging at the new normal like a sweater that wasn’t quite comfortable yet.

But as the saying goes, everything old is new again, a notion that Ad Lightning experienced first-hand on the frontlines of ad quality. As I’m about to discuss, fraudsters were still up to no good in Q4, relying on everything from old standards to newer malicious horizons as their assault on publishers, platforms, consumers, and stakeholders continued full throttle.
Malicious Browser Extensions and Redirects and Trojans, Oh My!
Continuing a trend we’ve seen for a while now, malicious browser extensions and the redirects they often trigger remained at the top of our blocked list in Q4, collectively accounting for over half of our total blocks. In fact, as you can see from the following table, browser extensions and redirects dominated the bad ad landscape in Q4.
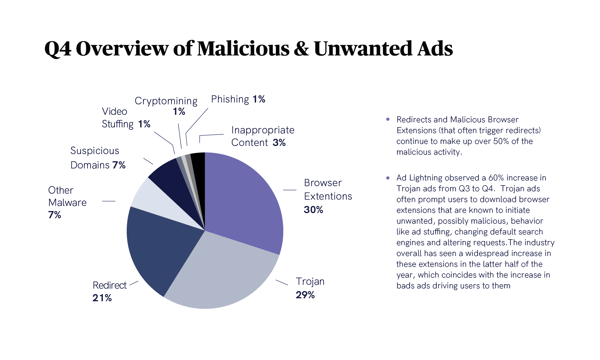
I want to draw your attention to second place on that list, though – trojan ads. Obviously, they were within a malicious hair of taking the malvertising crown from browser extensions. In fact, we saw a 60% increase in trojans from Q3 to Q4 to place them in that lofty position.
Of course, just as with redirects, there’s a direct link between browser extensions and our Q4 silver medalist. Trojan ads are well-known to lure users into downloading extensions that initiate unwanted, possibly malicious behavior like ad stuffing, changing default search engines, and altering requests.
The industry saw an overall, widespread increase in these extensions in the latter half of the year, aligning with the increase in bad ads driving users to them. It’s not a coincidence that the top three types of bad ads we blocked in Q4 – malicious browser extensions, trojans, and redirects – often work hand in hand.
Put another way, trojan ads drive the malicious browser extensions that make redirects such a common ad quality issue. And we fully expect to see more of this devious, harmful relationship between the three continue in 2021.
Malicious Behavior Peaked Early in the Quarter
Diving a bit deeper into our blocking data for Q4, we also see that total malicious behavior was at its highest rates earlier in the quarter.
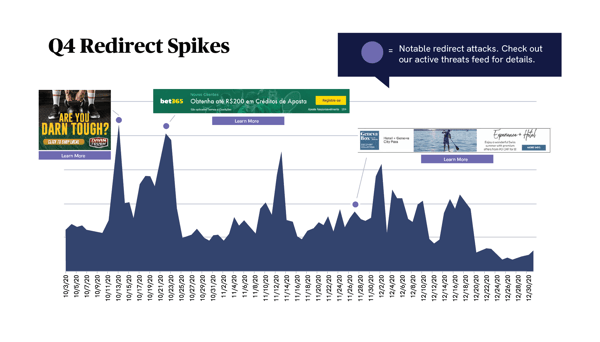
For instance, the first significant peak in the blocking data occurred during the October 10-12 weekend, primarily driven by three separate, potent redirect campaigns. Similarly, the two malicious campaigns resulting in the second major data peak, this time over the October 24-27 weekend, also surpassed any block volume we saw for the remainder of the quarter.
Besides the sheer size of these two massive spikes, perhaps what’s most disconcerting is the variety of different techniques the underlying campaigns used. From malicious scripts and steganography tactics to fake landing pages targeting several different industries, bad actors were their usual creative selves in finding gaps in the ecosystem to exploit.
Threat Spotlight: Steganography
One of the malicious techniques I mentioned in those fourth quarter blocking spikes, steganography, is of particular note given how quickly we saw its use evolve in 2020. In Q4, we saw the advanced use of steganography continue to be a common redirect tactic, with a handful of dormant campaigns from the summer re-emerging with vengeance.
Further, bad actors’ use of steganography – hiding malicious code in image files – became increasingly more sophisticated and frequent since the summer, mid-year months due to its ability to evade certain pre-scanning techniques.
From our vantagepoint, it’s obvious that fraudsters continue to invest immense time and resources into evading detection. And the results are obvious given the rapidly advancing obfuscation techniques, fingerprinting, wrapper detection, and debugger detection we saw over the course of the year.
Category Blocks Under the Spotlight
Largely due to the overwhelming success we had in blocking redirects for our partners in 2020, Q4 also saw many publishers and platforms focusing their attention toward category blocking – and for good reason.
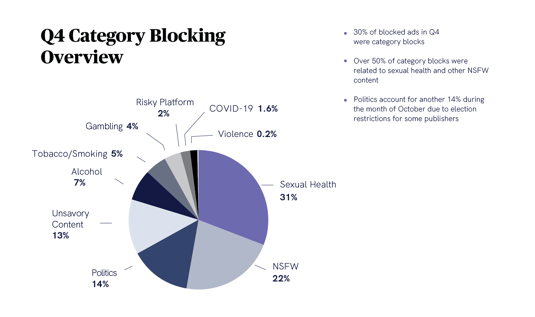
30% of our Q4 blocked ads were category blocks, with over 50% of those coming specifically from sexual health and other NSFW content. Naturally, since Q4 also encompassed a significant election, many publishers also used election category restrictions, amounting to 14% of total category blocks.
Fraudsters Changed Their Lumps of Coal Schedules
Lastly, I wanted to point out a subtle change we found in malicious activity across Q4. Typically, we see fraudsters target the weekends since there are fewer adops people in the office on those days. However, most likely because of the holidays, 60% of malicious attacks occurred between Sunday and Wednesday in Q4.
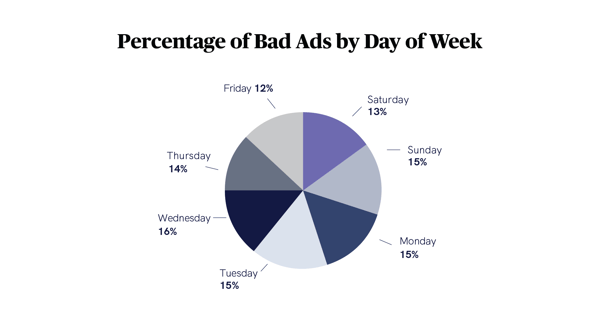
Also, following the same logic as the common weekend attacks with adops out-of-the-office, our time-of-day data reveals that fraudsters preferred the hours between midnight and 4 am, when everyone without cranky toddlers were fast asleep.
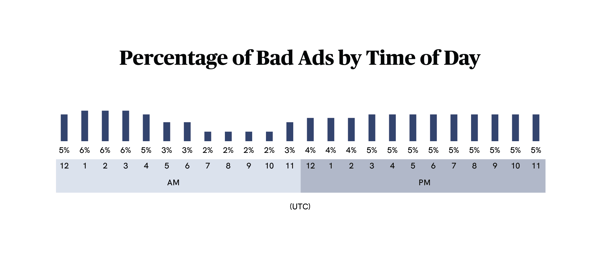
While we expect to see these malicious trends continue into 2021, there are other factors that will come into play as well. As I’ve discussed elsewhere, things like compliance, categorization, video ads, and other hot button subjects will also drive headlines going forward.
Thankfully for the industry, Ad Lightning will have an effective solution for all, along with our industry-best ad quality solution. As our partners will attest, there’s something to be said for having true experience and expertise in your corner.


.png)